Crowd sourcing is a very profitable field. It is basically making other people do you r work for you, for free. Google has nailed this type of work. Based on the data they collect they make applications more user friendly, in doing so they have essentially cut out the middle man. Google Maps is one application people use daily that helps everyone. As the official Google Blog mentions, "When we combine your speed with the speed of other phones on the road,
across thousands of phones moving around a city at any given time, we
can get a pretty good picture of live traffic conditions". So some companies do use it for good. A lot of industries are getting nailed for this because they are abusing their customers and collecting sensitive data. Google knows not to step into that realm as the backlash could cost them billions of dollars.
Data mining is quite the lucrative field if you're a small company though. A lot of apps ask for access to your location and spending habits. amazon uses this to show you things that maybe you would like to buy. It allows for them to move more product and get more companies on their supply list.
google blog:
http://googleblog.blogspot.com/2009/08/bright-side-of-sitting-in-traffic.html
Sunday, December 15, 2013
Gaming
The evolution of computer graphics has been incredible. Not
too long ago, people were still looking at very basic 2 dimensional objects on
screens with low resolution. With the
tremendous growth in the field of computer graphics, the same games have become
hundred times better with high resolution. Computer graphics has helped kids
characters come to life and bring a new level of excitement into their lives.
We see one of the first online games, doom, as the first
stepping stone into what is now massive online gameplay. Doom was made to play
online with other people back when dial up internet technology was present. From
there we have moved to having thousands to millions of players online. World of
Warcraft alone boasts more than 10 million players. From computer gaming we
moved onto created console gaming as there was such a demand for it. Now they are so ingrained in our society that the NSA even spies on them, as Chris Morris mentions in his blog, "
The 82-page document suggests that government agencies have long been concerned that terrorists or criminal groups could use virtual worlds to 'hide in plain sight'"
The 82-page document suggests that government agencies have long been concerned that terrorists or criminal groups could use virtual worlds to 'hide in plain sight'"
Console gaming is by far one of the most popular types of
gaming. With games like halo and call of duty being the front runners of the
industry. As we’ve gone through the years we have moved from 2D games to 3d
games. Players are now able to see individual blades of grass and bullets piecing
walls.
The next frontier is actually making the player experience the
action of the game. Oculus makes a headset that actually makes you feel like
you are in the game. It is a excting new field and im curious to see where it
goes.
Chris Morris's Blog
http://games.yahoo.com/blogs/plugged-in/report-nsa-spying-online-games-175511620.html
Chris Morris's Blog
http://games.yahoo.com/blogs/plugged-in/report-nsa-spying-online-games-175511620.html
Saturday, December 7, 2013
They're watching
There have always been conspiracy's in the world. Big foot, area 51, and yes, there are people who don't believe the moon exists. Some of these conspiracy's are truly wacky. however some things that you think are impossible are sometimes being done without your knowledge and are very real. For this we look at the NSA.
Recently thanks to a former employee of the NSA, Edward Snowden, leaking files of what the NSA is actually doing. The NSA since as early as 2008, have been spying on American citizens, the people who fund them. They have been collecting phone calls, messages, and yes your internet traffic. It's not only us that they're spying on though, its the rest of the first world. Information on other countries leaders and people of importance. This is a huge invasion of privacy that we as a nation, have done nothing about. I don't think people quite understand how invasive this is. the NSA has the capability of turning on your laptop camera and microphone without your knowledge and recording your most private moments. They have your search history and access to your data. even most encrypted data is accessible.As mentioned in Washingtons blog one of formal NSA officials that helped make the surveillance system admits that "We are, like, that far from a turnkey totalitarian state." It's funny in a way that the money we earn and pay taxes on, is funding a agency that is spying on us, so in turn, we are spying on us, and giving the information to less than reputable people.
So what do we as a country do about this? I'm not ok with my money going into this program. I think the money would be better spent on social programs or to schools or anything that gives the US more infrastructure. We only have ourselves as citizens to blame for this intrusive government program, and we will have to be the ones to fix it as well.
Washington's blog:
http://www.washingtonsblog.com/2013/12/former-top-nsa-official-now-police-state.html
Recently thanks to a former employee of the NSA, Edward Snowden, leaking files of what the NSA is actually doing. The NSA since as early as 2008, have been spying on American citizens, the people who fund them. They have been collecting phone calls, messages, and yes your internet traffic. It's not only us that they're spying on though, its the rest of the first world. Information on other countries leaders and people of importance. This is a huge invasion of privacy that we as a nation, have done nothing about. I don't think people quite understand how invasive this is. the NSA has the capability of turning on your laptop camera and microphone without your knowledge and recording your most private moments. They have your search history and access to your data. even most encrypted data is accessible.As mentioned in Washingtons blog one of formal NSA officials that helped make the surveillance system admits that "We are, like, that far from a turnkey totalitarian state." It's funny in a way that the money we earn and pay taxes on, is funding a agency that is spying on us, so in turn, we are spying on us, and giving the information to less than reputable people.
So what do we as a country do about this? I'm not ok with my money going into this program. I think the money would be better spent on social programs or to schools or anything that gives the US more infrastructure. We only have ourselves as citizens to blame for this intrusive government program, and we will have to be the ones to fix it as well.
Washington's blog:
http://www.washingtonsblog.com/2013/12/former-top-nsa-official-now-police-state.html
Wednesday, December 4, 2013
Domo Erigato, Mr. Roboto
Artificial intelligence is becoming more and more prominent in our culture. AI is any software that makes a decision based on what information it has gathered. this includes things like autofill on your smart phones all the way to IBM's Watson. Artificial intelligence has made our lives easier when trying to do the most mundane tasks such as texting or trying to find the fastest route to where we want to go.
We look at a higher level AI such as IBM's Watson. Watson was created to show off IBM's technology on the game show jeopardy where he beat every single human opponent. He is so powerful he can process 500 gigabytes, the equivalent of a million books, per second. This is the power of AI currently. Someday we will reach the stage at which robots preforms surgeries and other difficult tasks we as humans take years to learn how to do, and they will learn it over the course of a few hours. As Steve Hamm mentions in his blog, " This vision is not science fiction. Because of today’s advances in computing, we’ll hold learning machines in our hands in the foreseeable future. "
We already have robots on mars gathering samples of rock and satellites maintaining orbit of the earth.

AI has a lot to offer us and the more advanced technology becomes the more applications of AI we can apply to our lives. Someday our most advanced tasks will be done by AI and then what? where does that place us as humans?
Steve Hamm's Blog
http://asmarterplanet.com/blog/2013/12/ibms-5-5-future-computers-will-learn.html
We look at a higher level AI such as IBM's Watson. Watson was created to show off IBM's technology on the game show jeopardy where he beat every single human opponent. He is so powerful he can process 500 gigabytes, the equivalent of a million books, per second. This is the power of AI currently. Someday we will reach the stage at which robots preforms surgeries and other difficult tasks we as humans take years to learn how to do, and they will learn it over the course of a few hours. As Steve Hamm mentions in his blog, " This vision is not science fiction. Because of today’s advances in computing, we’ll hold learning machines in our hands in the foreseeable future. "
We already have robots on mars gathering samples of rock and satellites maintaining orbit of the earth.
AI has a lot to offer us and the more advanced technology becomes the more applications of AI we can apply to our lives. Someday our most advanced tasks will be done by AI and then what? where does that place us as humans?
Steve Hamm's Blog
http://asmarterplanet.com/blog/2013/12/ibms-5-5-future-computers-will-learn.html
Tuesday, December 3, 2013
Computer Science
Computers have been been growing smaller and faster as each generation passes. It's hard to imagine that computers used to be entire buildings and the internet didn't even exist! fast forward 60 years and our current computers are immensely more powerful than the ones that used to take up entire buildings. Technology has come so far that its hard to imagine its roots. \
The only way to input into a computer used to be punch cards. You may have had to go through 10 punch cards to do one mathematical operation. now we do millions of operations in our laptop and desktop computers per second. Old computers used to use vacuum tubes to store information, if a tube went bad your calculations would be off. Transistors replaced vacuum tubes in computers starting when computers became household items. They
no longer needed to be the size of a building, just the size of your computer now.
Mobile devices also changed due to advances in technology. People used to have huge phones the size of your head to talk to people through a wireless network. Now do we not only have phones that fit in your palm, they have screens you can touch as well. Touch screens and games with bright magnificent colors that play through a story. It truly is a wonder how far we have come in such a short amount of time.
The programming languages used in these devices get more and more powerful as time goes on as well. One of the oldest languages, C is still very much in use today. In Kasia Mikoluk blog she mentions C as "C is powerful, stable, and easily available on virtually all platforms." Strict limitations on memory and how to send and retrieve information has only made these languages more efficient at their tasks.
Without the study of computer science none of this would be possible. Algorithms and efficiency issues pondered over for hours upon hours. Where computer science is taking technology is not truly known. its only limited to what our imaginations can create.
Kasia Mikoluk Blog:
https://www.udemy.com/blog/best-programming-language/
The only way to input into a computer used to be punch cards. You may have had to go through 10 punch cards to do one mathematical operation. now we do millions of operations in our laptop and desktop computers per second. Old computers used to use vacuum tubes to store information, if a tube went bad your calculations would be off. Transistors replaced vacuum tubes in computers starting when computers became household items. They
no longer needed to be the size of a building, just the size of your computer now.
Mobile devices also changed due to advances in technology. People used to have huge phones the size of your head to talk to people through a wireless network. Now do we not only have phones that fit in your palm, they have screens you can touch as well. Touch screens and games with bright magnificent colors that play through a story. It truly is a wonder how far we have come in such a short amount of time.
The programming languages used in these devices get more and more powerful as time goes on as well. One of the oldest languages, C is still very much in use today. In Kasia Mikoluk blog she mentions C as "C is powerful, stable, and easily available on virtually all platforms." Strict limitations on memory and how to send and retrieve information has only made these languages more efficient at their tasks.
Without the study of computer science none of this would be possible. Algorithms and efficiency issues pondered over for hours upon hours. Where computer science is taking technology is not truly known. its only limited to what our imaginations can create.
Kasia Mikoluk Blog:
https://www.udemy.com/blog/best-programming-language/
Sharing is caring
file sharing is when one person shares another file with another person on their computer. This effectively makes a copy of this file. This has come under scrutiny by companies as a form of stealing. However instead of charging for theft, companies are charging people with copy-right infringement(a far harsher crime).
 A very popular way to share files online is through bit-torenting sites. With bit-torrents you download parts of a file from a set of computers who have the same file. It's a very fast and efficient way of downloading files. However for it to work a multitude of computers must have the file and allow streaming of that file.This is under scrutiny by companies because only one person needs to buy their software for everyone to have it. They intimidate people into not sharing files by suing small families for large sums of money. A family's son was sued for downloading 12 songs off a bit torrent site and was successfully sued for 645,000 dollars. If he had bought the songs he would have paid 12 dollars. This Disgusting practice has become common over the past few years to where is some small businesses whole business plan.
A very popular way to share files online is through bit-torenting sites. With bit-torrents you download parts of a file from a set of computers who have the same file. It's a very fast and efficient way of downloading files. However for it to work a multitude of computers must have the file and allow streaming of that file.This is under scrutiny by companies because only one person needs to buy their software for everyone to have it. They intimidate people into not sharing files by suing small families for large sums of money. A family's son was sued for downloading 12 songs off a bit torrent site and was successfully sued for 645,000 dollars. If he had bought the songs he would have paid 12 dollars. This Disgusting practice has become common over the past few years to where is some small businesses whole business plan.
The reality of it is that these bit torrent sites help companies more than they hurt them. Heck they even add jobs to the market, as mentioned in Utorrents Blog, " For the past few months our engineers have been hard at work developing a mobile BitTorrent app that is worthy of the name “µTorrent.” In order to live up to our high standards, we knew that the app would need to be fast, lightweight, powerful and better than anything else currently on the market." Thanks to bit-torrent sites company products get far more recognition than they would have if they weren't on these sites. If people like a product they will pay for that product. What these companies are doing to small familys is both wrong and immoral. The music and movie industry are huge perpetrators in this now common act of suing. I still fail to see how a movie downloaded for 20 dollars is suddenly worth 2 million if it's torrented.
Utorrents blog:
http://blog.utorrent.com/
 A very popular way to share files online is through bit-torenting sites. With bit-torrents you download parts of a file from a set of computers who have the same file. It's a very fast and efficient way of downloading files. However for it to work a multitude of computers must have the file and allow streaming of that file.This is under scrutiny by companies because only one person needs to buy their software for everyone to have it. They intimidate people into not sharing files by suing small families for large sums of money. A family's son was sued for downloading 12 songs off a bit torrent site and was successfully sued for 645,000 dollars. If he had bought the songs he would have paid 12 dollars. This Disgusting practice has become common over the past few years to where is some small businesses whole business plan.
A very popular way to share files online is through bit-torenting sites. With bit-torrents you download parts of a file from a set of computers who have the same file. It's a very fast and efficient way of downloading files. However for it to work a multitude of computers must have the file and allow streaming of that file.This is under scrutiny by companies because only one person needs to buy their software for everyone to have it. They intimidate people into not sharing files by suing small families for large sums of money. A family's son was sued for downloading 12 songs off a bit torrent site and was successfully sued for 645,000 dollars. If he had bought the songs he would have paid 12 dollars. This Disgusting practice has become common over the past few years to where is some small businesses whole business plan.The reality of it is that these bit torrent sites help companies more than they hurt them. Heck they even add jobs to the market, as mentioned in Utorrents Blog, " For the past few months our engineers have been hard at work developing a mobile BitTorrent app that is worthy of the name “µTorrent.” In order to live up to our high standards, we knew that the app would need to be fast, lightweight, powerful and better than anything else currently on the market." Thanks to bit-torrent sites company products get far more recognition than they would have if they weren't on these sites. If people like a product they will pay for that product. What these companies are doing to small familys is both wrong and immoral. The music and movie industry are huge perpetrators in this now common act of suing. I still fail to see how a movie downloaded for 20 dollars is suddenly worth 2 million if it's torrented.
Utorrents blog:
http://blog.utorrent.com/
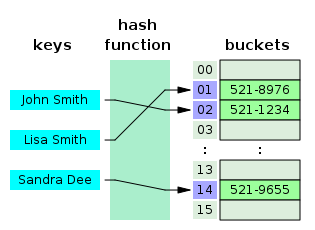
How do we store information?
How we store information is a big deal in the computing world. It lets us access information in a timely matter and get what we need. In the computing world, all information is stored in som
e kind of data structure. When you look up your friends on facebook or linked-in, all that information is stored and accessed using algorithms. Information is stored in various data structures such as B-trees, graphs, hash tables, and arrays.
What kind of information is being stored and our limitations will tell us what data structure we should use. Different data structures for minimum storage size may be an array or linked list. however the search time for an item in the list isnt as great as another data structure. So with each data structure there are trade offs. There is no overall perfect data structure for all information. If the want a fast sorting algorithm it may take up more more space than one that takes longer with a smaller space requirement. In a blog written by
Andy Lim, he mentions memory issues and constraints of different systems, he says"
These two architectures lead to various pros and cons relative to each other and to the standard matrix format."
Data Structures are the core foundation on which to program. You cant get by without knowing these things. Every piece of technology you use has some kind of association with data structures and algorithms. In short, you need to know Data Structures to be a Computer Science major, it is the foundation of modern computing.
Andy Lim Blog:
http://blog.custora.com/tag/data-structures/
e kind of data structure. When you look up your friends on facebook or linked-in, all that information is stored and accessed using algorithms. Information is stored in various data structures such as B-trees, graphs, hash tables, and arrays.
 |
| Quick-Sort |
Andy Lim, he mentions memory issues and constraints of different systems, he says"
These two architectures lead to various pros and cons relative to each other and to the standard matrix format."
Data Structures are the core foundation on which to program. You cant get by without knowing these things. Every piece of technology you use has some kind of association with data structures and algorithms. In short, you need to know Data Structures to be a Computer Science major, it is the foundation of modern computing.
Andy Lim Blog:
http://blog.custora.com/tag/data-structures/
Sunday, October 27, 2013
Is hacking Ethical?
This week I'm going to talk about hackers. Not to be confused with when you leave your Facebook logged in and your friend comes and makes an embarrassing post. That's not hacking. Hacking has to do with different inputs to crack a password and access an account, not an account you happened to leave logged in. With the air cleared on that there are different types of hackers. White hat hackers hack for a corporation to make that corporations product is secure. They do penetration testing to make sure other color hats don't break into their system or program. The next color of hat is black hat hackers. Black hat hackers break into systems typically for personal gain. They steal identities, credit cards, etc. to either sell or to create chaos for a company or person. Gray hat hackers are the gray area of hacking. Gray hat hackers will try to compromise a system just to well... test it. They will alert the company of the security programs if they find them usually. However there have been a lot of anger towards gray hat hackers. Companies have started suing them for exposing the security problems instead of thanking them or fixing the breaches. These people are who hack for fun, not for profit by like a white or black hat hacker.
 With all of that laid out. There is a convention for hackers called Def-con. Def-con is a hacking convention where companies and hackers and until most recently NSA would attend to show off their latest tools they've developed. One particular tool that was incredibly interesting is a program that listens to wireless traffic. Dependent on the port that information was sent by, the program could determine what each device was on the network. The best part of this program was, no one would know if you were listening. as in your device wouldn't intercept and repeat the signal, it would receive the broadcasted and message without anyone knowing the wiser that it was listening. There has been a worldwide outcry over our government hacking other governments information along with its own citizens information. People cry foul as this would be consider black hat hacking. The government refuses to tell us what they're using the information or gathering it in the first place. It also hurt a lot of big Tech businesses here in America. as mentioned in an aritcile by Cecilia Kang and Ellen Nakashima, "Cisco has said it is already seeing customers, especially those
overseas, back away from U.S.-branded technology after documents
revealed that the NSA enlisted tech firms and also secretly tapped into
their data hubs around the world as the agency pursued terrorism
suspects." After these revelation they were barred from attending Def-con this last year.
With all of that laid out. There is a convention for hackers called Def-con. Def-con is a hacking convention where companies and hackers and until most recently NSA would attend to show off their latest tools they've developed. One particular tool that was incredibly interesting is a program that listens to wireless traffic. Dependent on the port that information was sent by, the program could determine what each device was on the network. The best part of this program was, no one would know if you were listening. as in your device wouldn't intercept and repeat the signal, it would receive the broadcasted and message without anyone knowing the wiser that it was listening. There has been a worldwide outcry over our government hacking other governments information along with its own citizens information. People cry foul as this would be consider black hat hacking. The government refuses to tell us what they're using the information or gathering it in the first place. It also hurt a lot of big Tech businesses here in America. as mentioned in an aritcile by Cecilia Kang and Ellen Nakashima, "Cisco has said it is already seeing customers, especially those
overseas, back away from U.S.-branded technology after documents
revealed that the NSA enlisted tech firms and also secretly tapped into
their data hubs around the world as the agency pursued terrorism
suspects." After these revelation they were barred from attending Def-con this last year.
There are so many different types of hacking that it may be construed to people only thinking its bad. Hackers Anonymous are always pegged as the bad guys even when they expose corruption in our government. Sometimes hackers are bad, sometimes they're good, sometimes they're the unsung heroes that we need to expose the truth. hacking gives us knowledge and security, if used for the right reasons.
Cecilia Kang and Ellen Nakashima Article:
http://www.post-gazette.com/news/nation/2013/12/18/Tech-CEOs-to-Obama-NSA-s-hacking-hurt-our-business/stories/201312180059
 With all of that laid out. There is a convention for hackers called Def-con. Def-con is a hacking convention where companies and hackers and until most recently NSA would attend to show off their latest tools they've developed. One particular tool that was incredibly interesting is a program that listens to wireless traffic. Dependent on the port that information was sent by, the program could determine what each device was on the network. The best part of this program was, no one would know if you were listening. as in your device wouldn't intercept and repeat the signal, it would receive the broadcasted and message without anyone knowing the wiser that it was listening. There has been a worldwide outcry over our government hacking other governments information along with its own citizens information. People cry foul as this would be consider black hat hacking. The government refuses to tell us what they're using the information or gathering it in the first place. It also hurt a lot of big Tech businesses here in America. as mentioned in an aritcile by Cecilia Kang and Ellen Nakashima, "Cisco has said it is already seeing customers, especially those
overseas, back away from U.S.-branded technology after documents
revealed that the NSA enlisted tech firms and also secretly tapped into
their data hubs around the world as the agency pursued terrorism
suspects." After these revelation they were barred from attending Def-con this last year.
With all of that laid out. There is a convention for hackers called Def-con. Def-con is a hacking convention where companies and hackers and until most recently NSA would attend to show off their latest tools they've developed. One particular tool that was incredibly interesting is a program that listens to wireless traffic. Dependent on the port that information was sent by, the program could determine what each device was on the network. The best part of this program was, no one would know if you were listening. as in your device wouldn't intercept and repeat the signal, it would receive the broadcasted and message without anyone knowing the wiser that it was listening. There has been a worldwide outcry over our government hacking other governments information along with its own citizens information. People cry foul as this would be consider black hat hacking. The government refuses to tell us what they're using the information or gathering it in the first place. It also hurt a lot of big Tech businesses here in America. as mentioned in an aritcile by Cecilia Kang and Ellen Nakashima, "Cisco has said it is already seeing customers, especially those
overseas, back away from U.S.-branded technology after documents
revealed that the NSA enlisted tech firms and also secretly tapped into
their data hubs around the world as the agency pursued terrorism
suspects." After these revelation they were barred from attending Def-con this last year.There are so many different types of hacking that it may be construed to people only thinking its bad. Hackers Anonymous are always pegged as the bad guys even when they expose corruption in our government. Sometimes hackers are bad, sometimes they're good, sometimes they're the unsung heroes that we need to expose the truth. hacking gives us knowledge and security, if used for the right reasons.
Cecilia Kang and Ellen Nakashima Article:
http://www.post-gazette.com/news/nation/2013/12/18/Tech-CEOs-to-Obama-NSA-s-hacking-hurt-our-business/stories/201312180059
Tuesday, September 24, 2013
How to Promote Yourself Online
Today's world revolves around technology and information online. One major shift we have seen in recent years is more and more companies are reviewing applicants online. There's no longer a job application you get from going to the business and filling out, it's all online. Not only is it all online resumes but also other forms of communication that show who you are. One particular social networking site is just for jobs and jobs alone. Linked in is a professional networking site that allows people to connect for business purposes. However, just like MySpace and Facebook, you create a linked in profile that shows your professional behavior, in other words, its your online resume.
How to sell it:
 Look at other peoples profiles, it will give you a general sense of what you should be putting up on your profile and what you should not be. One thing to consider is these people are your competition, you want to have what they have on their profile and more. Take their information and see if it can be represented better or in a different way.
Look at other peoples profiles, it will give you a general sense of what you should be putting up on your profile and what you should not be. One thing to consider is these people are your competition, you want to have what they have on their profile and more. Take their information and see if it can be represented better or in a different way.
It is your online Resume:
Remember that your LinkedIn profile is your online profile for all employers to look at. This means have a professional picture to use for your profile. As Michael Poh mentions in his blog "For LinkedIn, it is expected for your bio to reveal your experience and expertise, your educational background along with various accomplishments in your career." As in you should optimize each social network site for what that site is used for. No employer wants to look at your profile and you have a picture of you doing a keg-stand at a party you're way too old to be at. Keep it professional. List your skills and attributes and how they relate to your line of work. If you're a programmer applying for a job at programming for a car company, put cars as one of your interests. Be sure to write about yourself in your LinkedIn profile. Triple check for grammar and spelling mistakes, as it could be your undoing for a potential employer.
When you create this profile remember it represents you, but only the professional you. keep all the other information for Facebook and MySpace for expressing yourself.
Michael Poh's Bog:
http://www.hongkiat.com/blog/optimizing-online-presence-for-jobs/
How to sell it:
 Look at other peoples profiles, it will give you a general sense of what you should be putting up on your profile and what you should not be. One thing to consider is these people are your competition, you want to have what they have on their profile and more. Take their information and see if it can be represented better or in a different way.
Look at other peoples profiles, it will give you a general sense of what you should be putting up on your profile and what you should not be. One thing to consider is these people are your competition, you want to have what they have on their profile and more. Take their information and see if it can be represented better or in a different way.It is your online Resume:
Remember that your LinkedIn profile is your online profile for all employers to look at. This means have a professional picture to use for your profile. As Michael Poh mentions in his blog "For LinkedIn, it is expected for your bio to reveal your experience and expertise, your educational background along with various accomplishments in your career." As in you should optimize each social network site for what that site is used for. No employer wants to look at your profile and you have a picture of you doing a keg-stand at a party you're way too old to be at. Keep it professional. List your skills and attributes and how they relate to your line of work. If you're a programmer applying for a job at programming for a car company, put cars as one of your interests. Be sure to write about yourself in your LinkedIn profile. Triple check for grammar and spelling mistakes, as it could be your undoing for a potential employer.
When you create this profile remember it represents you, but only the professional you. keep all the other information for Facebook and MySpace for expressing yourself.
Michael Poh's Bog:
http://www.hongkiat.com/blog/optimizing-online-presence-for-jobs/
Wednesday, September 11, 2013
QR codes: why?
 QR codes are a relatively new form of advertising. They are these little
"two-dimensional (2-D) matrix code that belongs to a larger set of
machine-readable codes" - DENSO that companies use to promote whatever
they like really. They show up in magazines, posters, cereal boxes etc. that
you can scan with your smart phone or tablet. What they bring up is a mystery
until you scan it. They typically have phone numbers, a Facebook, a website, or
even a
QR codes are a relatively new form of advertising. They are these little
"two-dimensional (2-D) matrix code that belongs to a larger set of
machine-readable codes" - DENSO that companies use to promote whatever
they like really. They show up in magazines, posters, cereal boxes etc. that
you can scan with your smart phone or tablet. What they bring up is a mystery
until you scan it. They typically have phone numbers, a Facebook, a website, or
even ablog that belongs to a user. The one I have included in this blog links to well... my blog. Professionals may use them on business cards to link to their website which has their resume posted.
Why Would I personally use it?
You can use it for whatever you like! There are a million different uses that are only limited by your imagination. I just used one for my blog, partially because hey I'm required to, but also because it’s interesting. You can prank your friends, mess with your coworkers, and advertise yourself! As I mentioned it’s a way that you can advertise yourself to people and this is a great way if you are advertising major. However, be careful with how much you rely on them, sometimes its too much of a hassle, as Graham Charlton says in his blog, "Make sure the QR code serves a purpose and adds to the user experience." What he means is don't post QR codes for every little thing! make their use efficient not bothersome. It shows that even the even though it’s barely 50% of people that scan QR codes, you still understand and can reach that group of people.
Cons of QR codes:
 The main problem with QR codes is something I mentioned before: it’s a
mystery to what they link to. QR codes can go to websites that contain
malicious code for your device or to some obscure inappropriate website. With
that said, that’s why there are only about 50% of people who scan them in
public. The ones posted in magazines and newspapers are more trusted but it
still comes down to the possibility of the QR code being unsafe. It's like
taking a trust fall with people you've never met and can only trust their
reputation.
The main problem with QR codes is something I mentioned before: it’s a
mystery to what they link to. QR codes can go to websites that contain
malicious code for your device or to some obscure inappropriate website. With
that said, that’s why there are only about 50% of people who scan them in
public. The ones posted in magazines and newspapers are more trusted but it
still comes down to the possibility of the QR code being unsafe. It's like
taking a trust fall with people you've never met and can only trust their
reputation.Overall....
Like I said though it’s a great way to advertise and take polls and gives you an easy way to link something you want people to know about. It still has its little quirks that every form of advertisement does. To skip over the market of people who do use QR codes would be a great loss to a company in potential followers.
Graham Charlton's Blog:
http://econsultancy.com/us/blog/62397-qr-codes-the-good-the-bad-and-the-ugly
Friday, September 6, 2013
The Science of Selling Yourself
Be Careful Selling Yourself
The internet is ever expanding in its capabilities and what
roles it plays in our lives. We see cell
phones become something almost
everyone had in 1995-2000. By 2005 everyone was texting their friends and using MySpace.com to express. This is where social networking began to become
huge. Now almost everybody I know has a linked-in or a Facebook account in
2013. It’s become such a necessity that it’s required to have one of these
accounts to get a job. To socialize and protect your identity are the two most
important things online.
Use Protection
 Kids, teenagers, young adults, and professionals use Facebook.com to share pictures, ideas and let people know about us. That being
said, how do you know if the person you’ve added on Facebook is really your
friend and not someone else posing as them? This is a major problem with online
profiles is that there is no verification for creating these profiles. I had
someone create a fake profile of me on Facebook once and harass my then
girlfriend, and Facebook did nothing to stop it even though I reported him.
People are also trying to scam you while you are on these social media sites
offering tempting rewards to steal your password or bank account numbers. Our
online identities are very vulnerable even though we don’t go out giving it
away on purpose. Back when the Boston bombing happened, social media site Reddit.com accused an innocent bystander of planting the homemade bombs,
slandering him and his family’s name.
Kids, teenagers, young adults, and professionals use Facebook.com to share pictures, ideas and let people know about us. That being
said, how do you know if the person you’ve added on Facebook is really your
friend and not someone else posing as them? This is a major problem with online
profiles is that there is no verification for creating these profiles. I had
someone create a fake profile of me on Facebook once and harass my then
girlfriend, and Facebook did nothing to stop it even though I reported him.
People are also trying to scam you while you are on these social media sites
offering tempting rewards to steal your password or bank account numbers. Our
online identities are very vulnerable even though we don’t go out giving it
away on purpose. Back when the Boston bombing happened, social media site Reddit.com accused an innocent bystander of planting the homemade bombs,
slandering him and his family’s name.
Socialize
 With that being said you need to sell yourself online to
people. You have to be very careful about what you say and who your audience is.
We see companies like go-daddy.com supporting legislation to censor the internet
lose a huge amount of business for its actions. The same thing happened to Rush
Limbaugh Losing a ton of sponsors after coming out against gay marriage. How
much information passes through social media is astonishing to say the least.
So securing your identity is important as If someone pretends to be you, you
could instantly be hated by a large sum of people. Facebook users have
something called a Klout score which measures your online influence based on
your posts, time spend online, and who you communicate with. Linked-in is a
social networking site for jobs in itself.
With that being said you need to sell yourself online to
people. You have to be very careful about what you say and who your audience is.
We see companies like go-daddy.com supporting legislation to censor the internet
lose a huge amount of business for its actions. The same thing happened to Rush
Limbaugh Losing a ton of sponsors after coming out against gay marriage. How
much information passes through social media is astonishing to say the least.
So securing your identity is important as If someone pretends to be you, you
could instantly be hated by a large sum of people. Facebook users have
something called a Klout score which measures your online influence based on
your posts, time spend online, and who you communicate with. Linked-in is a
social networking site for jobs in itself.
To sum it up
We see that it’s not optional to use social media to sell
ourselves but a requirement to be successful. Jason miller wrote in his blog about your linked in page as a " page to tell members what you do best and give them compelling reasons to follow you." You have to put yourself out
there, but you have to take precautions to keep your identity safe. As selling yourself on social media sites is
important, so is all of your personal information and everything else you may
store online. You have a Large digital footprint that needs to have shoes on at
all times. It's important to keep your personal image in person as well as online. This goes not only for people but for companies as well
http://www.socialmediaexaminer.com/linkedin-company-pages-marketing-tips/
http://www.socialmediaexaminer.com/linkedin-company-pages-marketing-tips/
Wednesday, August 28, 2013
Hello World!
Hello World! Or rather the SJSU CS 100w class and partners. My name is Jace Rose and I am a computer science major at SJSU. My expertise has always been putting the pieces together. In order to
solve a puzzle you always need all the pieces and to know what all the
pieces look like, so you can put them together. I've always loved building things, My favorite toy as a child and still is are Lego's. I find that as we grow up it's always important to keep our minds solving harder and larger problems. From lego's I moved onto bulding computers from the motherboard and up. From building computers I moved onto doing IT work and managing servers and user accounts. Now I've arrived at my true passion: Programming. The reason I love programming is because of the problem solving. Being able to look at a problem or an idea and bring it to life is the most exciting thing I have ever done. It's truly a thrill to be able to build programs and create a virtual world in which whatever you need you can create. I think that's what lures people into the major, the feeling of limitlessness.
Subscribe to:
Posts (Atom)